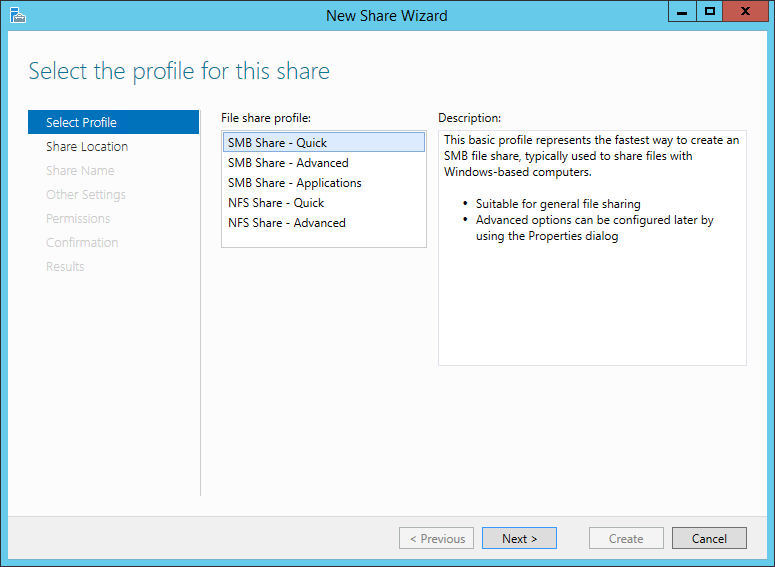
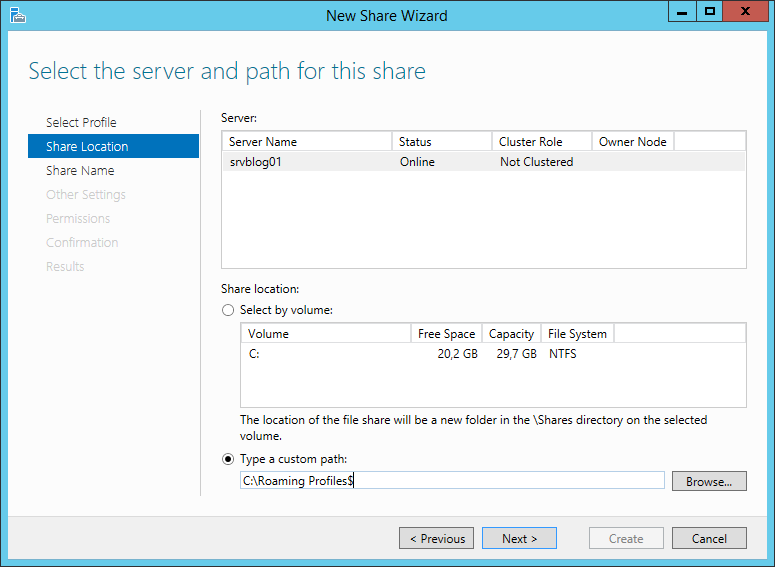
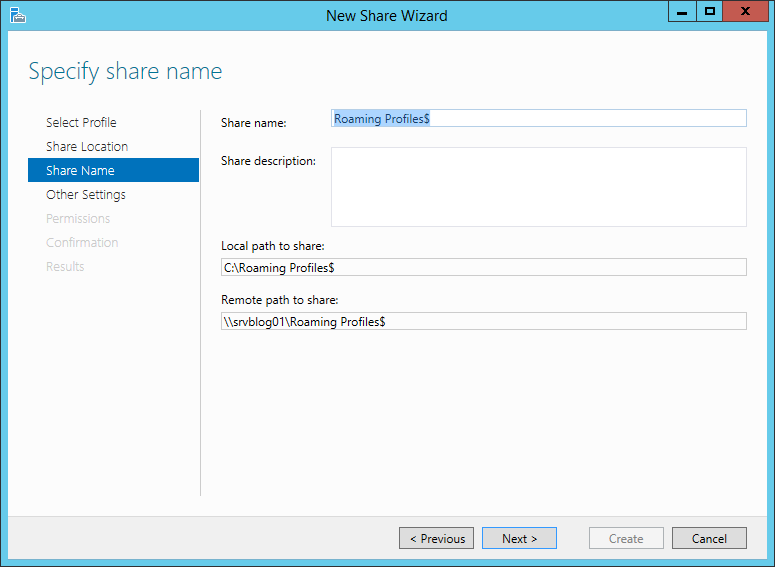
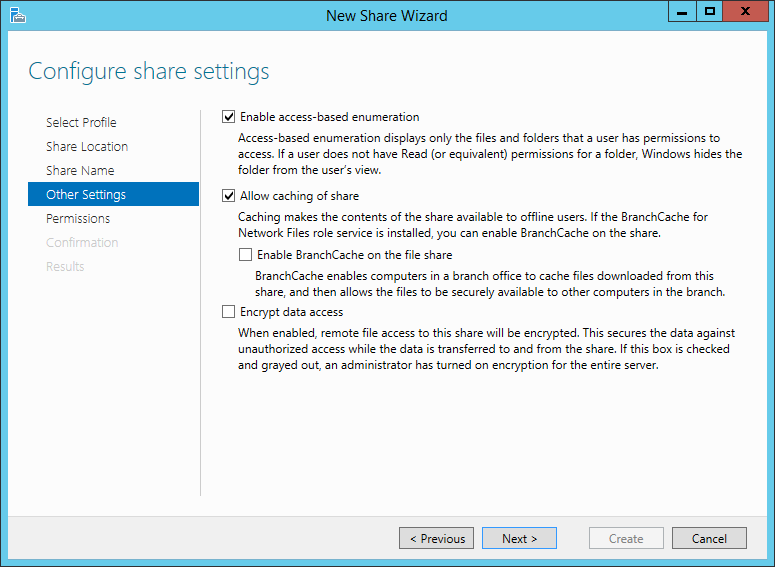
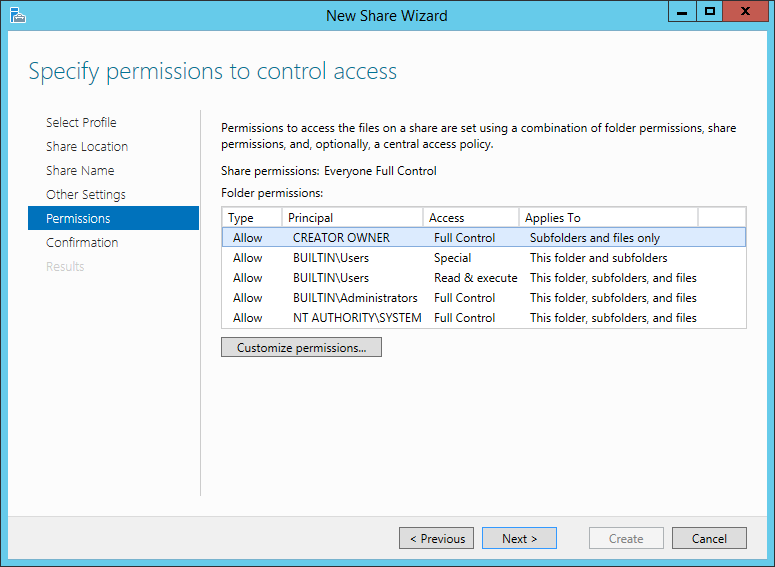
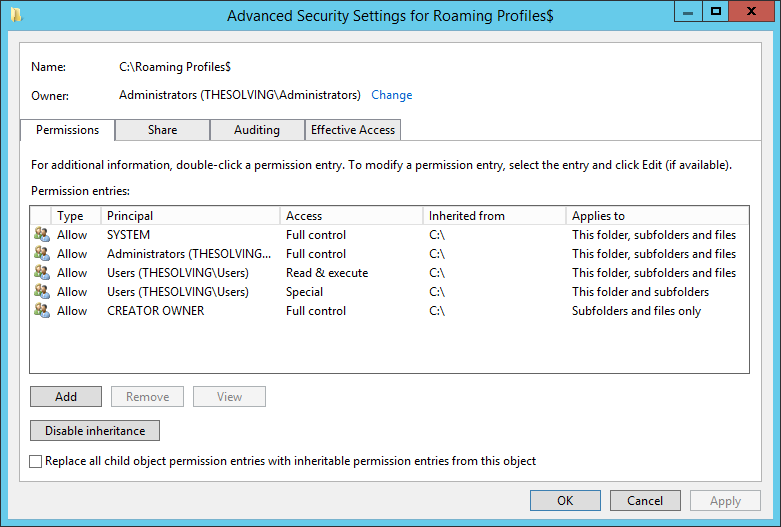
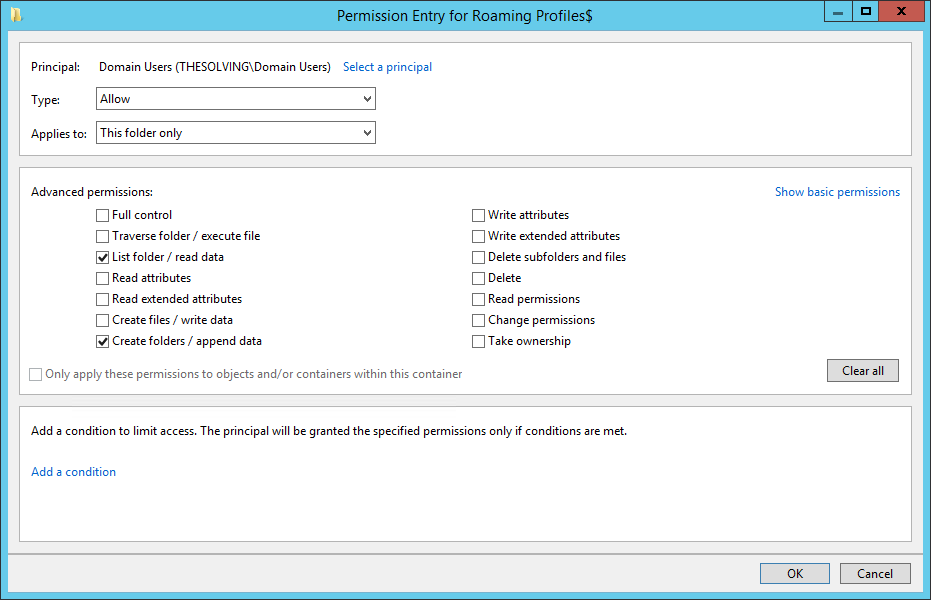
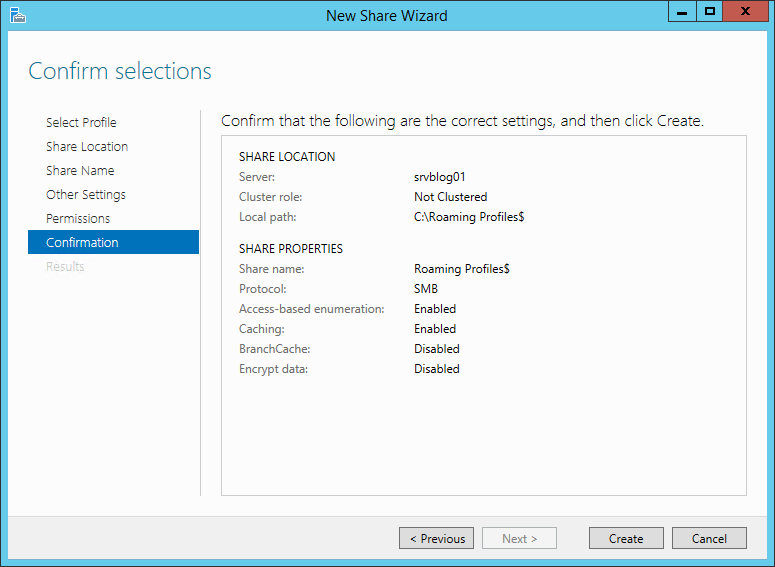
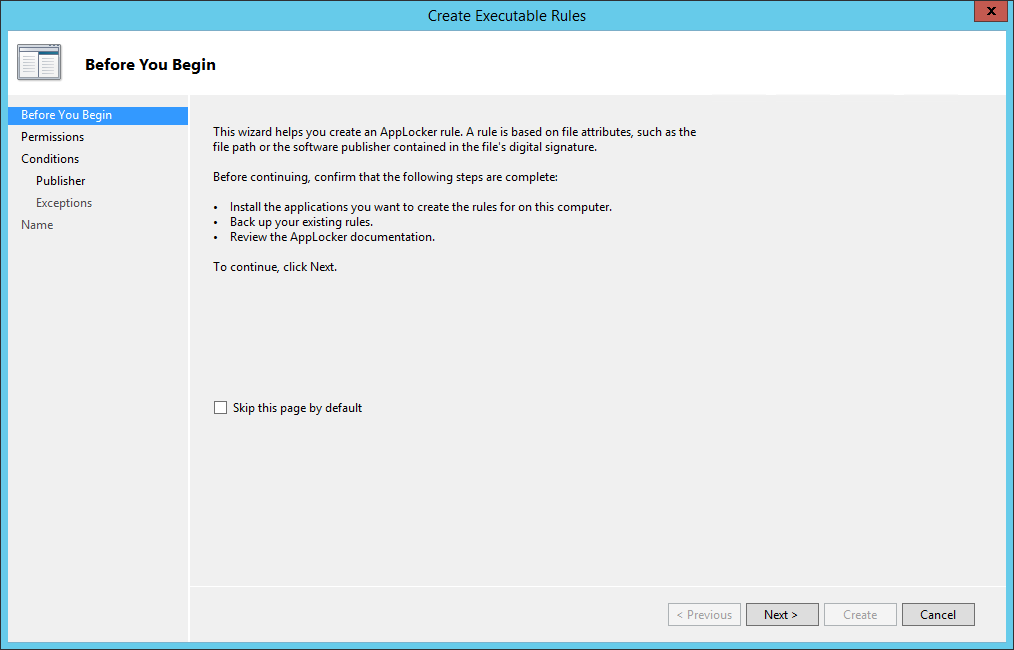
Thanks to the improvements of virtualization and storage technologies, it’s not difficult to clone a disk. A great advantage for disaster recovery, but also a potential risk for the security of your information.
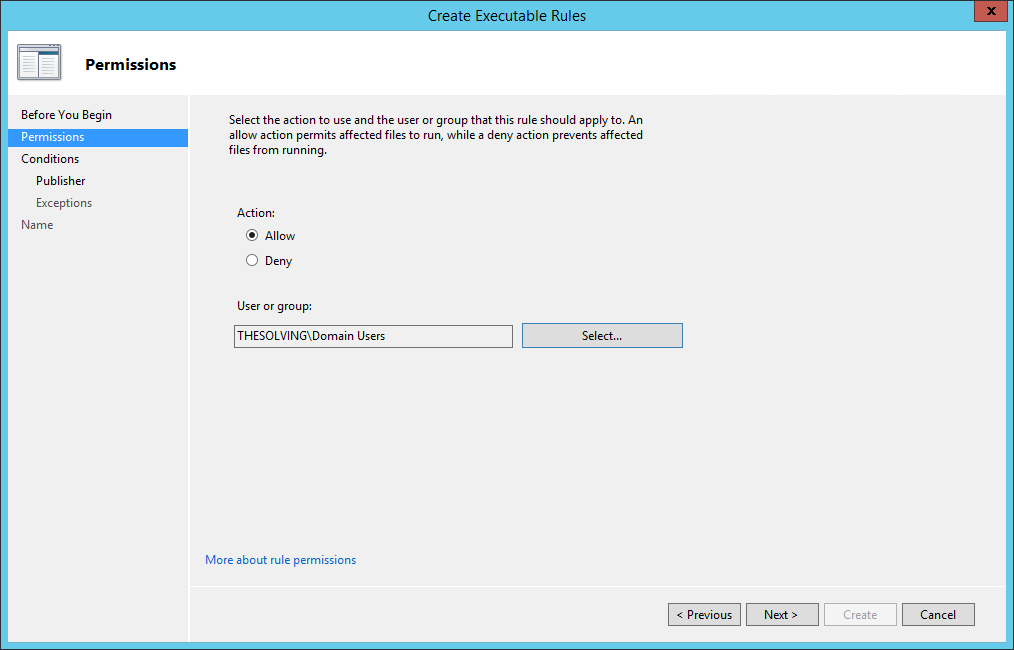
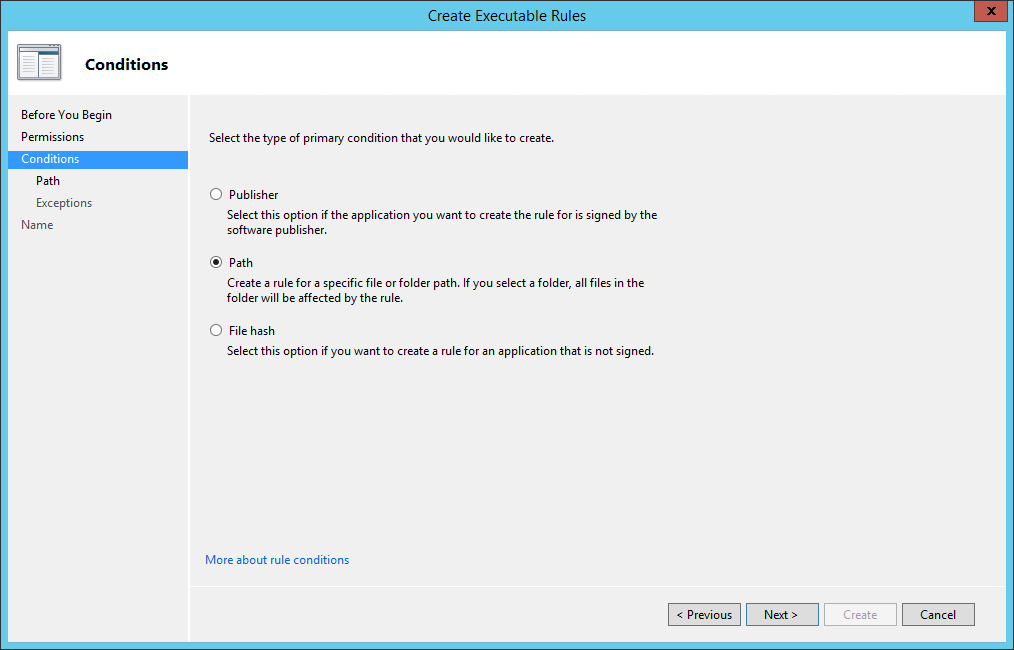
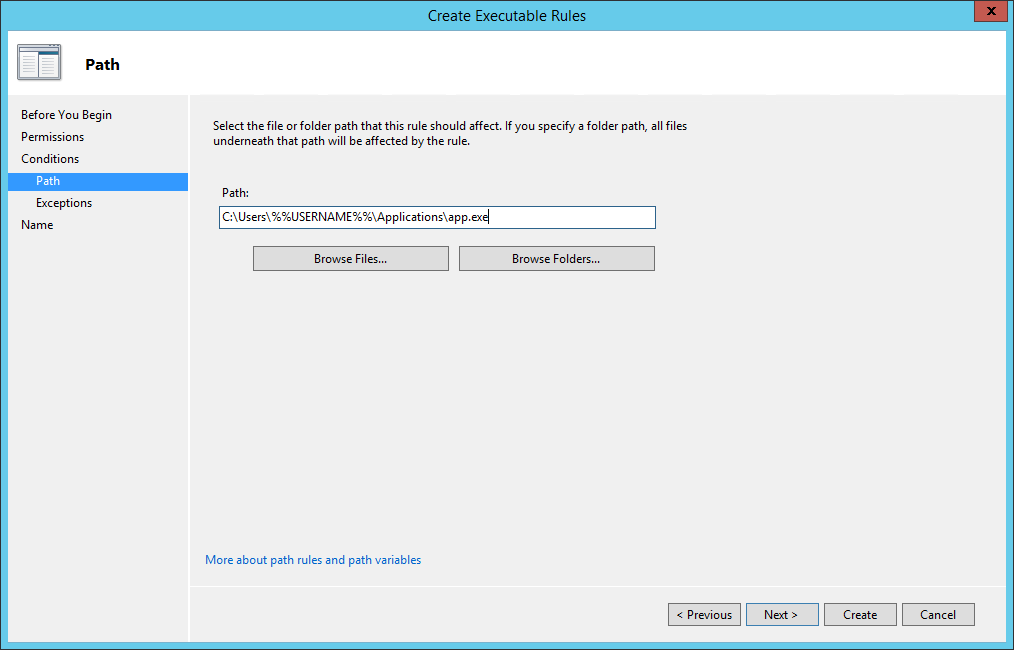
Microsoft allows to encrypt the disks of a server with a feature named BitLocker. We are going to see how you can enable BitLocker on a physical or virtual server to protect your company from data theft.
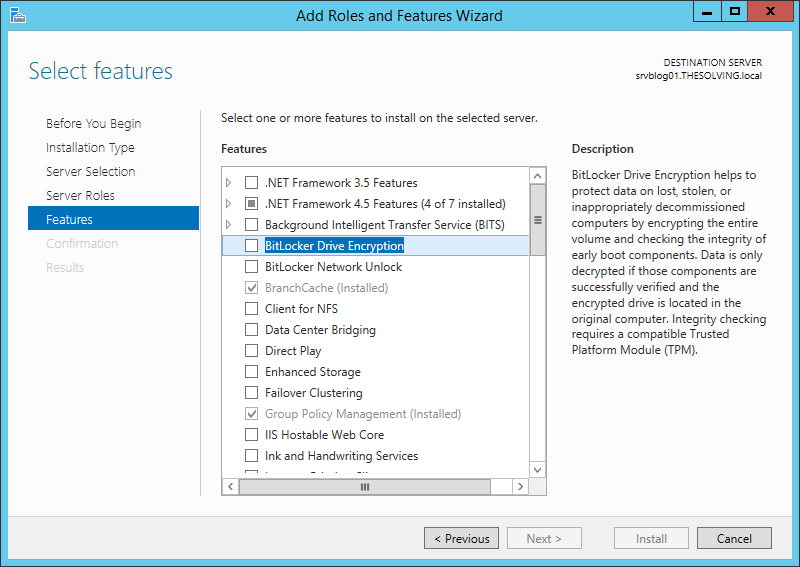
Install the BitLocker Drive Encryption feature with the Add Roles and Features Wizard:
You need to restart the system after the installation:
How to enable BitLocker on a virtual machine (without TPM)
You need the Trusted Platform Module (TPM) in order to take advantage of BitLocker encryption. Virtual machines don’t have the TPM module so you need to follow these two steps BEFORE configuring BitLocker (BitLocker must be installed on the server).
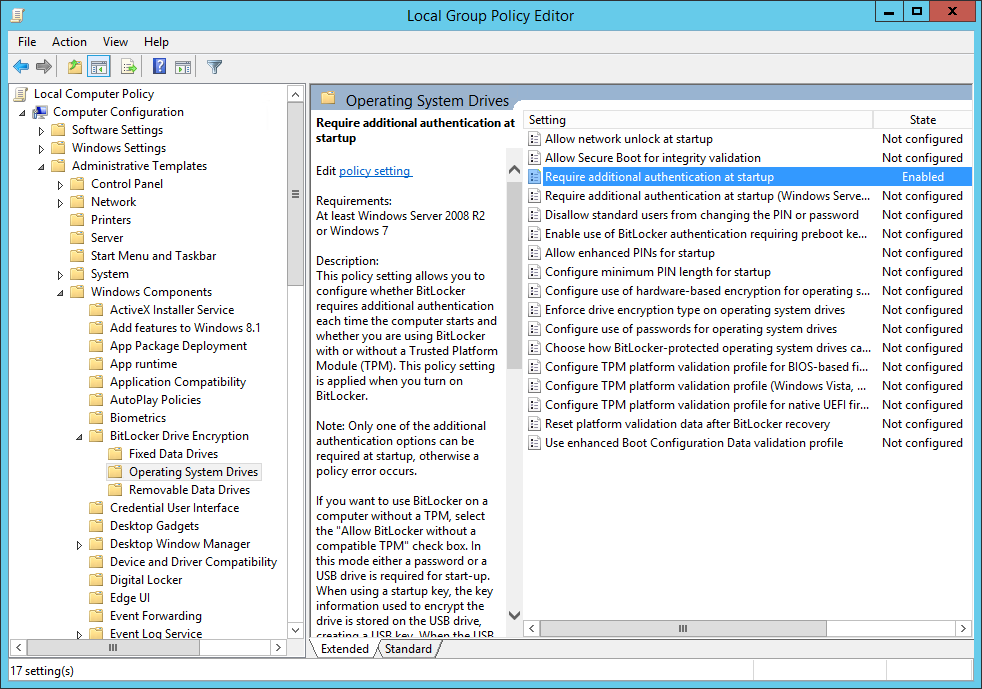
Open the Local Group Policy Editor (gpedit.msc) and go to
Computer Configuration/Administrative Templates/Windows Components/BitLocker Drive Encryption/Operating System Drives. Double-clickRequire additional authentication at startup:
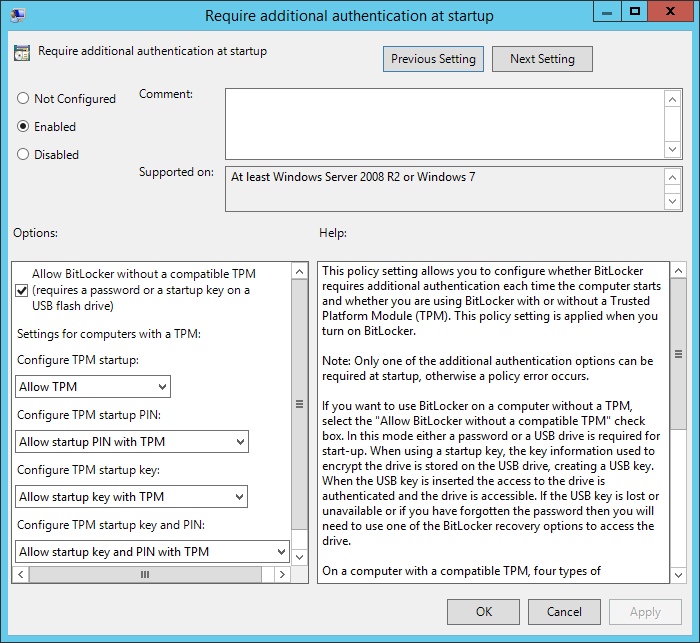
Select Enable and check Allow BitLocker without a compatibile TPM:
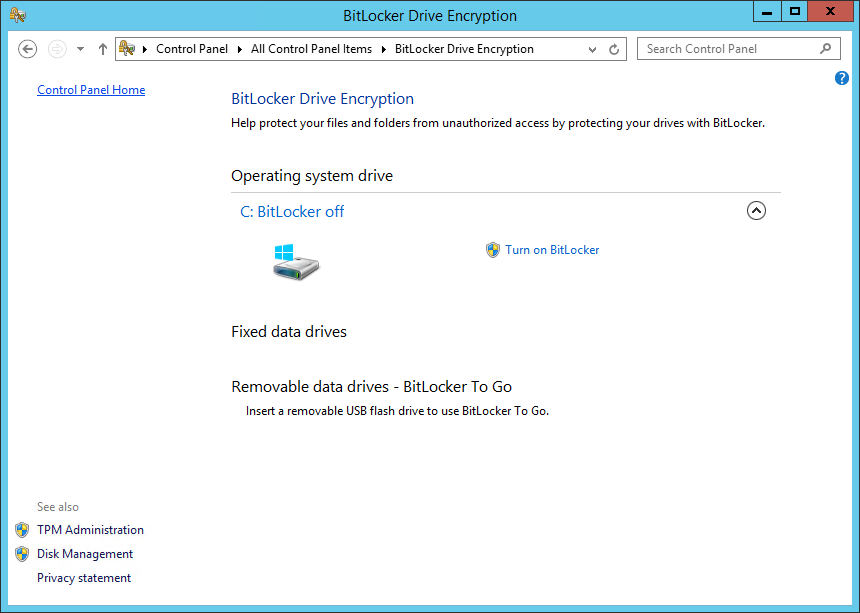
After a restart, open the Control Panel, you’ll find the BitLocker configuration panel. Open it and clickTurn On BitLocker:
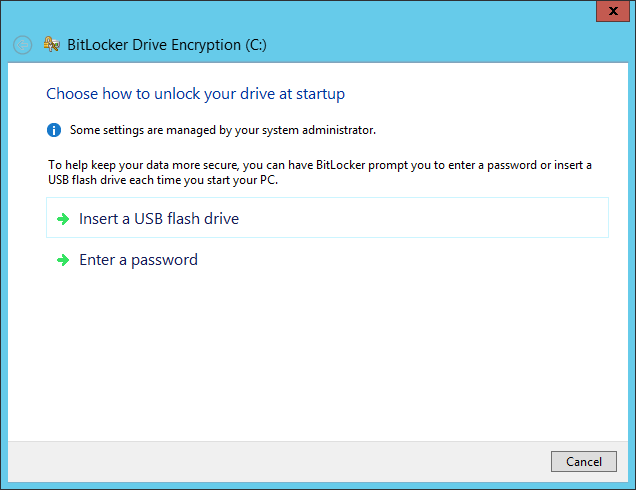
In this tutorial we used a VM, so a system without a TPM, and Windows aks us to configure an additional authentication at startup. We chose a password to protect the data, but we suggest to use a USB flash drive instead. With a flash drive you don’t have to enter the password at every server restart, just leave the USB drive plugged and you’ll be fine:
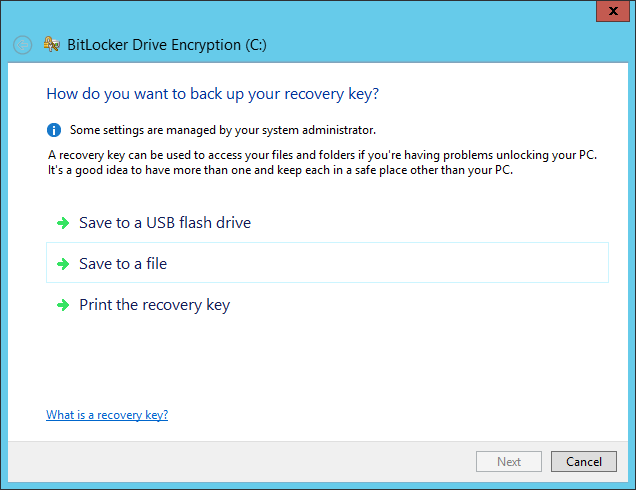
A recovery key can save you from big troubles. We printed it for security reasons:
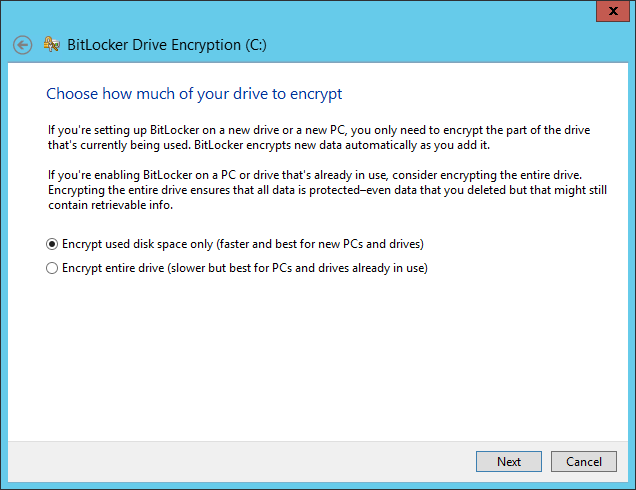
Choose the encryption mode more suited for your disks:
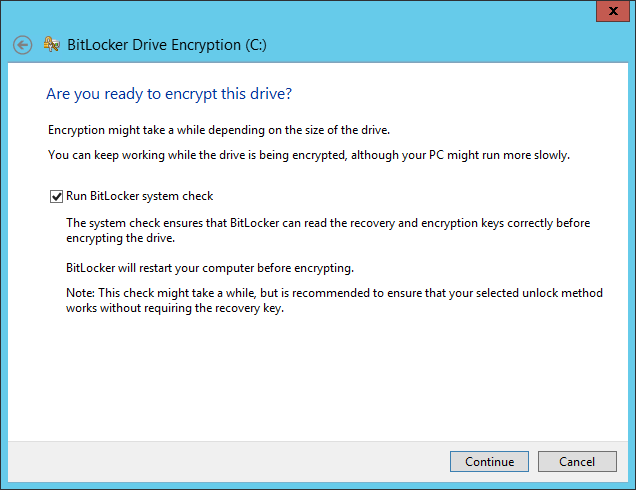
Click Continue:
Restart the system:
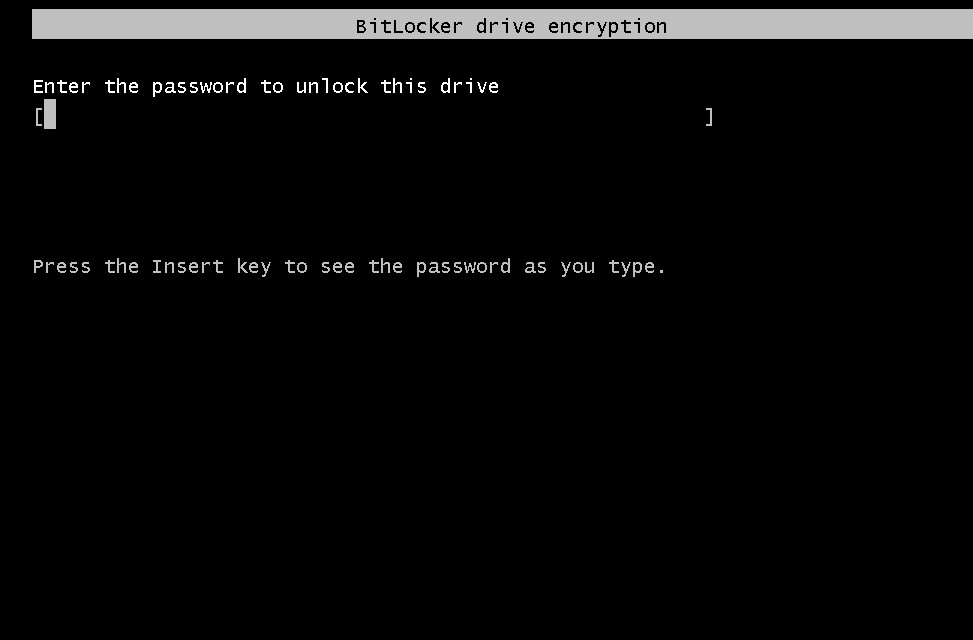
At the next boot you’ll be “forced” to enter the password or plug the USB flash drive. After the Windows start BitLocker will begin the encryption process: